Vulnerability Management
Protect your business with Cyber Fortify’s proactive Vulnerability Management services. Our experts identify, assess, and mitigate vulnerabilities to enhance your security posture and prevent potential threats.
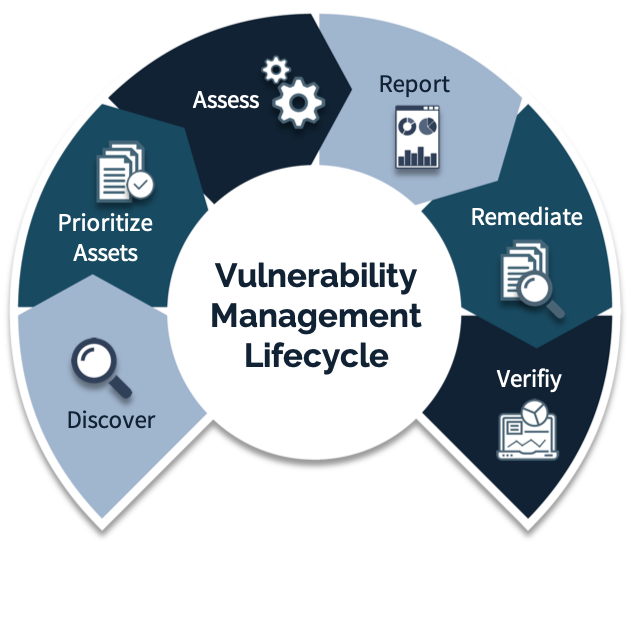


Investing in our Vulnerability Management services ensures that your organization remains secure by continuously identifying and addressing security weaknesses. Our team uses advanced tools and methodologies to conduct thorough vulnerability assessments and implement effective mitigation strategies.
Partner with Cyber Fortify to strengthen your security posture through comprehensive vulnerability management. We provide tailored solutions to address your specific security needs, ensuring continuous protection against potential threats.

Our vulnerability management service includes ongoing assessments to identify and address security weaknesses, keeping your organization secure.

We implement effective mitigation strategies to reduce the risk of exploitation and enhance your overall security posture.

Our team of security professionals provides detailed analysis and recommendations to help you prioritize and address vulnerabilities effectively.




 SOC Monitoring
SOC MonitoringOur team of skilled and experienced professionals provides continuous surveillance and analysis of network traffic, system logs, and security events to detect and respond to potential cybersecurity threats in real-time. We act as first responders and provide help with incident prevention, investigation, and remediation efforts.
See more Firewall Management
Firewall ManagementWe specialize in configuring, monitoring, and maintaining firewall infrastructure to keep your network secure. Our services include firewall rule management, log monitoring, configuration/policy migration, best practice assessment and hardware and software upgrades.
See more Penetration Testing
Penetration TestingIn the always evolving cybersecurity landscape it is important to get ahead and discover weaknesses in your applications and network that could be exploited by malicious actors. Our team of experts can help you assess your security posture, validate defense mechanisms, and prioritize remediation efforts to improve your security posture.
See more