Penetration Testing
Identify and fix security vulnerabilities with Cyber Fortify’s expert Penetration Testing services. Our comprehensive assessments help protect your business from cyber threats and ensure your systems are secure.


Investing in our Penetration Testing services provides a thorough examination of your security defenses. Our team of skilled testers simulates real-world attacks to uncover vulnerabilities, providing you with detailed insights and actionable recommendations to strengthen your security.
Partner with Cyber Fortify to fortify your defenses against cyber threats. Our penetration testing services are designed to identify and address vulnerabilities, ensuring your systems are resilient and secure.

Our penetration testing service offers a detailed assessment of your security defenses, uncovering vulnerabilities that could be exploited by attackers.

We simulate real-world attacks to identify potential security gaps, helping you understand and address your vulnerabilities.

Our experts provide actionable insights and recommendations to help you strengthen your security posture and prevent future attacks.




 SOC Monitoring
SOC MonitoringOur team of skilled and experienced professionals provides continuous surveillance and analysis of network traffic, system logs, and security events to detect and respond to potential cybersecurity threats in real-time. We act as first responders and provide help with incident prevention, investigation, and remediation efforts.
See more Vulnerability Management
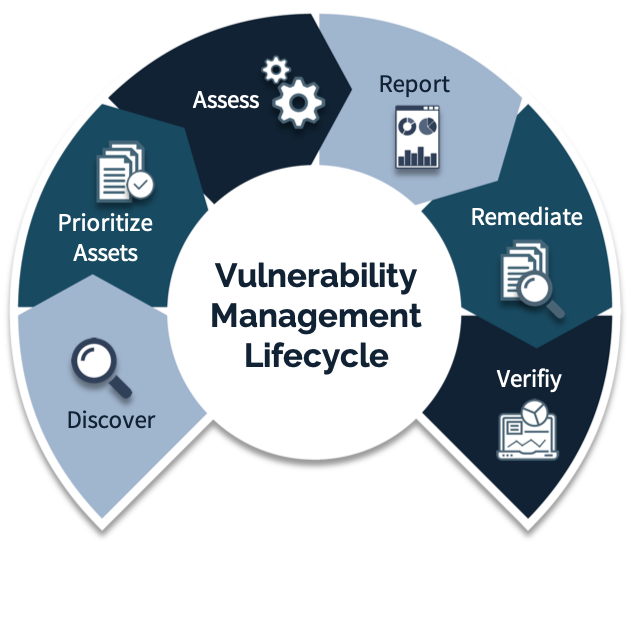
Vulnerability ManagementVulnerability management is an important part of the overall security program. With this in mind, we take proactive and continuous approach in identifying and remediating vulnerabilities to help your organization reduce its risk exposure. Our approach includes discovery, assessment, prioritization, remediation, verification, continuous monitoring, and reporting.
See more Firewall Management
Firewall ManagementWe specialize in configuring, monitoring, and maintaining firewall infrastructure to keep your network secure. Our services include firewall rule management, log monitoring, configuration/policy migration, best practice assessment and hardware and software upgrades.
See more