Firewall Management
Ensure robust network security with Cyber Fortify's comprehensive Firewall Management services. Our experts provide continuous monitoring and management to protect your business from cyber threats.


Investing in our Firewall Management services ensures that your network is safeguarded against unauthorized access and cyber threats. Our team of security professionals uses advanced technologies to configure, monitor, and manage firewalls, ensuring optimal performance and protection.
Partner with Cyber Fortify to enhance your network security through effective firewall management. We offer tailored solutions that align with your specific security needs, providing continuous protection for your critical assets.

Our firewall management service includes 24/7 monitoring to detect and block potential threats, ensuring your network remains secure at all times.

We ensure that your firewalls are configured correctly to provide maximum protection against cyber threats, minimizing vulnerabilities and enhancing security.

Our proactive approach to firewall management helps prevent cyber attacks, safeguarding your business from potential security breaches and data loss.




 SOC Monitoring
SOC MonitoringOur team of skilled and experienced professionals provides continuous surveillance and analysis of network traffic, system logs, and security events to detect and respond to potential cybersecurity threats in real-time. We act as first responders and provide help with incident prevention, investigation, and remediation efforts.
See more Vulnerability Management
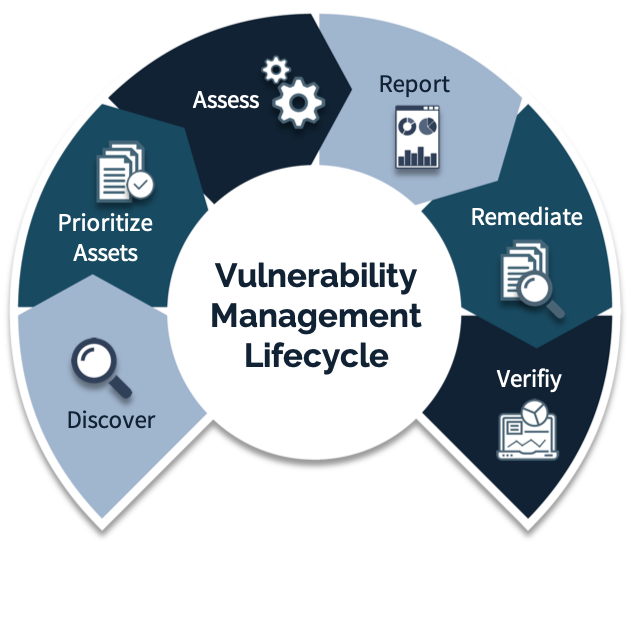
Vulnerability ManagementVulnerability management is an important part of the overall security program. With this in mind, we take proactive and continuous approach in identifying and remediating vulnerabilities to help your organization reduce its risk exposure. Our approach includes discovery, assessment, prioritization, remediation, verification, continuous monitoring, and reporting.
See more Penetration Testing
Penetration TestingIn the always evolving cybersecurity landscape it is important to get ahead and discover weaknesses in your applications and network that could be exploited by malicious actors. Our team of experts can help you assess your security posture, validate defense mechanisms, and prioritize remediation efforts to improve your security posture.
See more