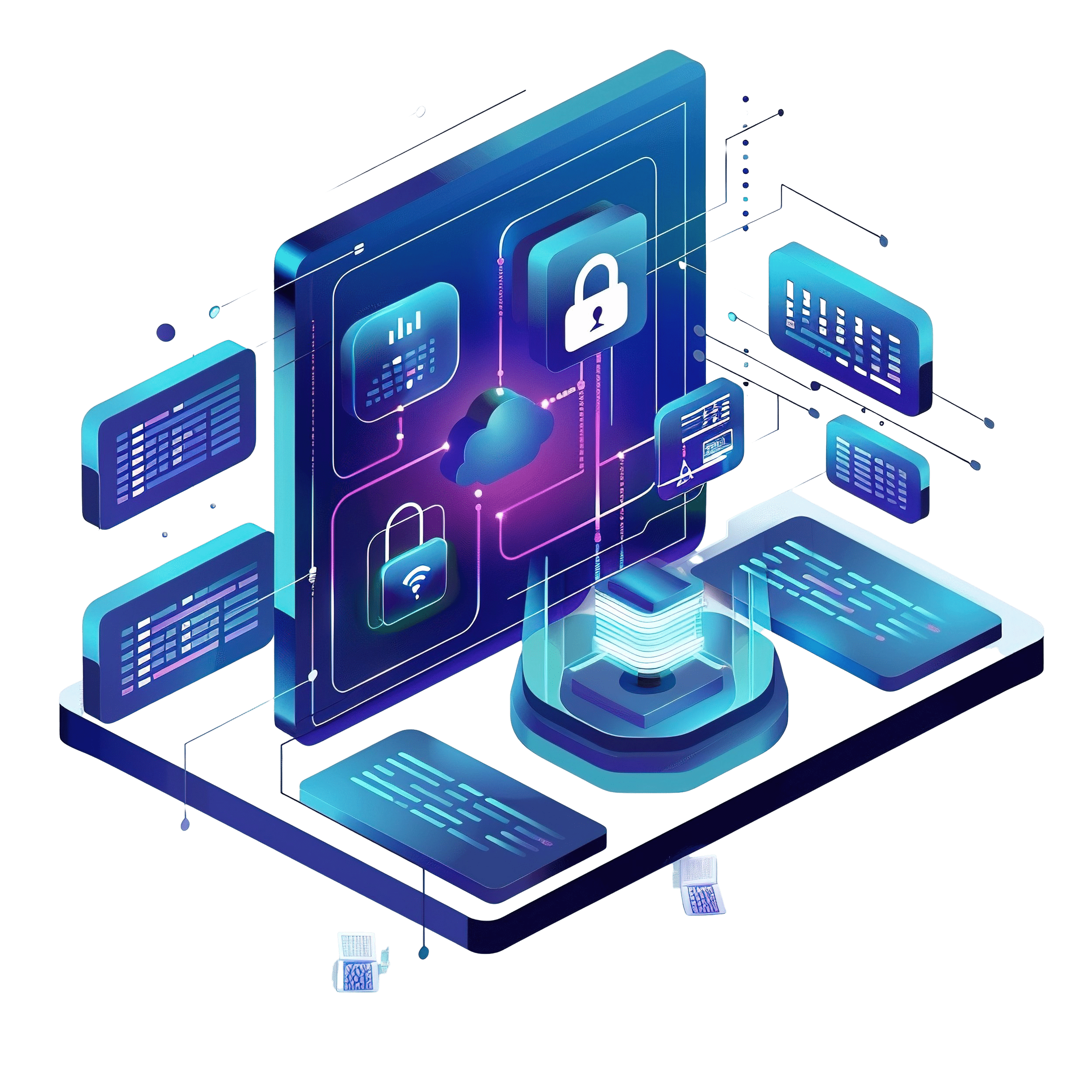
Firewall Management
Firewall ManagementWe specialize in configuring, monitoring, and maintaining firewall infrastructure to keep your network secure. Our services include firewall rule management, log monitoring, configuration/policy migration, best practice assessment and hardware and software upgrades.
See more Vulnerability Management
Vulnerability ManagementVulnerability management is an important part of the overall security program. With this in mind, we take proactive and continuous approach in identifying and remediating vulnerabilities to help your organization reduce its risk exposure. Our approach includes discovery, assessment, prioritization, remediation, verification, continuous monitoring, and reporting.
See more Penetration Testing
Penetration TestingIn the always evolving cybersecurity landscape it is important to get ahead and discover weaknesses in your applications and network that could be exploited by malicious actors. Our team of experts can help you assess your security posture, validate defense mechanisms, and prioritize remediation efforts to improve your security posture.
See more